Summary
In this post, I make a case that Sovrin not only conforms to Kim Cameron's Seven Laws of Identity, but constitutes the identity metasystem he envisioned in 2004.

In 2005, Microsoft's Chief Identity Architect, Kim Cameron wrote an influential paper called The Laws of Identity (PDF). Kim had been talking about and formulating these laws in 2004 and throughout 2005. It's no coincidence that Internet Identity Workshop got started in 2005. Many people were talking about user-centric identity and developing ideas about how we might be able to create an identity layer for the Internet. Fifteen years later, we're still at it, but getting closer and closer all the time.
The Internet was created without any way to identify the people who used it. The Internet was a network of machines. Consequently, all the identity in Internet protocols is designed to identify machines and services. People used the Internet through some institution (their company or university) and were part of that institution's administrative identity system. This can still be seen in the format of email addresses that identify both recipient and sender as someone@someplace. As the Internet grew to include people who weren't formally associated with an institution, every Web site and service created their own administrative identity domains. The result is the fractured plethora of identifiers, policies, and user experiences that constitute digital identity in 2019.
An Identity Metasystem
In his paper, Kim asks why it's so hard to create an identity layer for the Internet and answers his own question:
Mainly because there is little agreement on what it should be and how it should be run. This lack of agreement arises because digital identity is related to context, and the Internet, while being a single technical framework, is experienced through a thousand kinds of content in at least as many different contexts—all of which flourish on top of that underlying framework. The players involved in any one of these contexts want to control digital identity as it impacts them, in many cases wanting to prevent spillover from their context to any other. (emphasis in original)
Kim's answer is not a new identity system, but rather an identity metasystem. He describes the metasystem:
...different identity systems must exist in a metasystem. It implies we need a simple encapsulating protocol (a way of agreeing on and transporting things). We also need a way to surface information through a unified user experience that allows individuals and organizations to select appropriate identity providers and features as they go about their daily activities. The universal identity metasystem must not be another monolith. It must be polycentric (federation implies this) and also polymorphic (existing in different forms). This will allow the identity ecology to emerge, evolve and self-organize.
This is an excellent description of Sovrin. Sovrin is not a company or an identity provider. Rather, Sovrin is a set of protocols and a network that allows multiple identity providers (polycentric) to provide identity credentials to anyone for any purpose (polymorphic).
Let's look at how Sovrin stacks up as a universal identity metasystem that supports Kim's laws of identity.
1. User Control and Consent
Technical identity systems must only reveal information identifying a user with the user’s consent.
As a self-sovereign, multi-source identity system, Sovrin is architected so that the identity owner is structurally part of exchanging verifiable credentials1. This is enforced by the default to use non-correlatable, decentralized identifiers (DIDs) to establish relationships between identity owners, credential issuers, and credential verifiers. Since there is no universal identifier in Sovrin, the identity owner is the only legitimate point of correlation.
The ledger plays a role in putting the identity owner in control by providing a decentralized means for the credential verifier to obtain the information it needs to validate the legitimacy of the credential. As a result, the system avoids creating a back channel from verifier to issuer that might be used to exchange information about the identity owner without her consent.
The only personally identifying information (PII) available to the credential verifier is the information that the identity owner has consented to provide to the verifier.
Besides the control that credential exchange provides identity owners, people are not locked into a single provider for tools. They can choose from multiple, interoperable tools to use their Sovrin-based credentials. Sovrin is a public network that anyone can use. The network is architected to resist censorship that might deny people the control they need to use their digital credentials however they like.
2. Minimal Disclosure for a Constrained Use
The solution which discloses the least amount of identifying information and best limits its use is the most stable long term solution.
In Sovrin, credentials are issued to identity owners. But identity owners do not share the credential with the verifier. Presenting the entire credential would reveal more information than is necessary. Instead, the identity owner presents a zero-knowledge proof of the information the verifier needs. The ability to limit the information presented from a credential is important to maintaining privacy through the principle of minimal disclosure.
The credential verifier can verify the credential proof by looking at the credential definition on the ledger, retrieving the public DID and associated DID Document of the issuer, and using the public key in the DID Document to check the signature of the credential to ensure it hasn’t been tampered with. The verifier can also cryptographically verify that the credential was issued to the identity owner. As part of making a proof from the credential, the identity owner also proves that it has not been revoked by referencing the revocation registry, which is also available on the ledger.
3. Justifiable Parties
Digital identity systems must be designed so the disclosure of identifying information is limited to parties having a necessary and justifiable place in a given identity relationship.
As a multi-source identity system, Sovrin provides the means for each party in an identity transaction to play their role without the aid or assistance of an intermediary. Consider the following diagram that shows Alice receiving a credential from her employer and proving information about her employment to her bank.
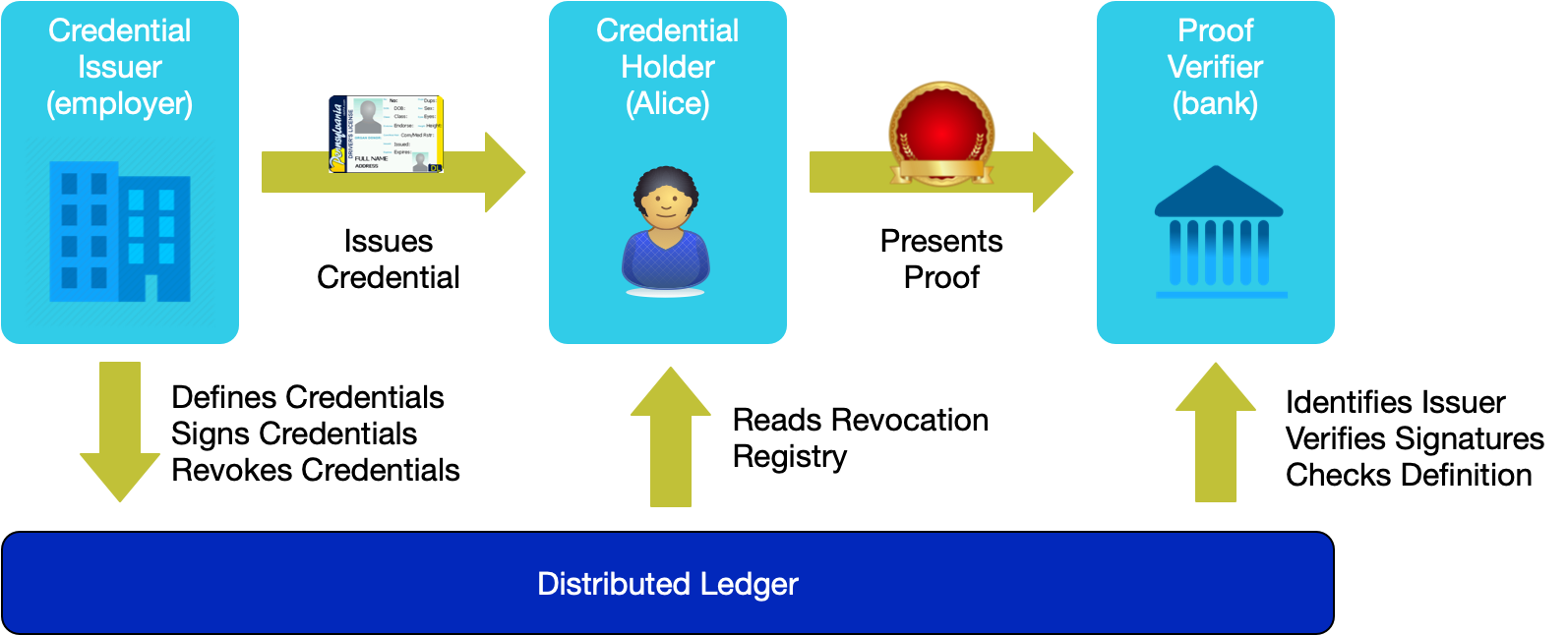
The only parties to the transaction are the three that need to be part of the transaction: Alice, her employer, and her bank. No other person or institution is party to the transaction. The ledger is run by validator nodes and one of more of those nodes might see the reads and writes to the ledger, but these are not correlatable and involve the public identifiers and information that the credential issuer used to create the credential definition.
4. Directed Identity
A universal identity system must support both "omni-directional" identifiers for use by public entities and "unidirectional" identifiers for use by private entities, thus facilitating discovery while preventing unnecessary release of correlation handles.
Sovrin supports both public ("omni-directional" in Kim's terminology) and private ("unidirectional") decentralized identifiers. Public DIDs are written to the ledger and available for anyone to look up. Private DIDs are not written to the ledger, but rather maintained in pairwise relationships between parties in peer-to-peer agents that are under the control of identity owners.
In the preceding diagram, the credential issuer, Alice's employer, has a public DID. A public DID is necessary to issue credentials since the verifier will want to look up the issuer as part of verifying the credential. The bank likely also has a public identifier but it plays no role in this credential exchange. Alice has exchanged private DIDs with both her employer and the bank. These private DIDs form the basis for the cryptographic relationship that Alice has with these institutions. The DIDs that the employer and bank give to Alice are also private, meant just for the relationship with Alice. The employer and bank created private DIDs to represent themselves to Alice, rather than using their public DIDs.
The use of public and private DIDs allows public discovery where necessary (the credential issuer) and prevents the correlation of records that credential issuer and verifier might have about the identity owner, this protecting her PII. The parties in a relationship can use the private DIDs and their associated public keys to mutually authenticate. Private DIDs are GDPR compatible since they are not shared on an immutable ledger.
5. Pluralism of Operators and Technologies
A universal identity system must channel and enable the inter-working of multiple identity technologies run by multiple identity providers.
Sovrin is a multi-source identity system. This means that rather than a single-source provider of identity credentials, as has been the norm for the Internet, anyone can issue any kind of credential for any purpose. Sovrin doesn't give you an identity—it's not an identity provider. Rather Sovrin enables a rich ecosystem of third party credentials, just like in the physical world. These credentials can be mixed together to easily prove things to others.
Credential schemas can be authored by anyone. And anyone can use an existing schema to create a credential definition which combines the schema, issuer DID, and revocation registry ID. This means that credentials are flexible and decentralized. No one is in charge of deciding what credentials are allowed or disallowed. No central party says which credentials are valid and which are not. Instead, each issuer decides what to issue, each identity owner decides which credentials to carry and present, and each verifier decides which credentials to trust.
Credentials are structured using a standard and exchanged using open protocols. Anyone can build software to use these standards and protocols or build them into their own systems. As a result, Sovrin presents an identity metasystem that anyone can use for any purpose and integrate with any tool or identity system they already use.
Beyond credentials, Sovrin's architecture supports independent software agents to hold and process credentials as well as to perform identity transactions on the identity owner's behalf. These agents interoperate directly with each other as peers. Sovrin specifies the protocols that agents use so that agents from different vendors can work together and to support substitutability.
6. Human Integration
The universal identity metasystem must define the human user to be a component of the distributed system integrated through unambiguous human-machine communication mechanisms offering protection against identity attacks.
As we've seen, the identity owner is a structural part of the identity transactions in Sovrin. Sovrin is architected to make by-passing her very difficult.
Identity owners don't manage keys but manage relationships and credentials, familiar artifacts from the physical world. Key management is handled by the software, below the interface. The identity owner can see, manage, add, delete, select, and share credentials on their device in the same manner they do other digital artifacts like files and folders. Rather than a world of user names and passwords, identity owners work with digital representations of the same things they use for identity transactions in the physical world.
People establish Sovrin relationships within contexts they already understand (e.g. their bank's website or their employer's HR system). They store those relationships in an app that functions like an address book on their phone. The app also stores credentials, another familiar item rendered digitally in the app. Because these artifacts and the act of exchanging credentials is analogous to what people do in their every day lives, the process of doing so with Sovrin is familiar as well.
7. Consistent Experience Across Contexts
The unifying identity metasystem must guarantee its users a simple, consistent experience while enabling separation of contexts through multiple operators and technologies.
The user experience with Sovrin is dictated by the protocol. Regardless of who identity owners are exchanging credentials with or what software they're using, the process is unified and consistent. The user experience is supported by the actors and roles in the protocol and the actions that each can take. Further, the open source code provides reference code for the applications that helps vendors of products that participate in credential exchange to create consistent, interoperable experiences.
At the same time, the unified experience supports multiple credentials from multiple parties who make decisions in a decentralized way. A person can mix verifiable claims from multiple credentials to create an identity transaction that is right for any particular online context. By seeing familiar digital artifacts, selecting, mixing, and sharing them in that context, the identity owner can see exactly what is being requested and make informed choices about what to share without excessive effort.
Sovrin as an Identity Metasystem
Kim concludes:
Putting all the laws together, we can see that the request, selection, and proffering of identity information must be done such that the channel between the parties is safe. The user experience must also prevent ambiguity in the user‟s consent, and understanding of the parties involved and their proposed uses. These options need to be consistent and clear. Consistency across contexts is required for this to be done in a way that communicates unambiguously with the human system components.
As users, we need to see our various identities as part of an integrated world which none the less respects our need for independent contexts.
Sovrin is architected to meet these needs and provide the kind of unified digital identity experience that Kim envisioned. When I read what Kim wrote almost 15 years ago, I get the feeling that he was a being from the future, telling us things that most of us were not prepared to understand for some time. I know I wasn't. The concepts and ideas that Kim laid out in the Seven Laws and follow-on work (PDF) provide a blueprint for understanding how we can really solve the problem of identity on the Internet.
Sovrin is the identity metasystem that Kim wrote about. I believe that creating and using an identity metasystem with the properties that Kim describes will have far reaching economic and functional impact. More importantly, I think the implications that it has for privacy, security, and human freedom and dignity cannot be overstated. When we look back, I think we'll all be surprised that it took us so long to build. I urge you to join us in making it a reality.
End notes:
- The word credential is used here where Kim used the word "claim." Technically a credential is a collection of claims. The credentials might be the kinds of things we typically think of as a credential, but might also be things that aren't often thought of that way like an airline boarding pass or a prescription for medicine. The world is full of credentials.
Photo Credit: Law Books from Max Pixel (CC0 1.0)




