Summary
I'm attended the Hyperledger Global Forum this last week–all virtual. I spoke on DIDComm and the Self-Sovereign Internet. If you're not up to speed with DIDComm and how it creates a secure overlay network on TCP/IP, you should be. I consider it one of the most important things to come out of the SSI movement.
Autonomic Identifiers
The foundation of the self-sovereign internet is built on autonomic identifiers. I'm going to speak about Peer DIDs here, but KERI and other systems provide autonomic identifiers that serve just as well.
Identity systems provide the means to remember, recognize, and rely on other parties in a relationship. To do so, they use identifiers, convenient handles that name the thing being remembered.
Identifiers are issued to or created by a controller (e.g. Alice) who, by virtue of knowing the authentication factors (e.g. password, key fob, cryptographic key), can make authoritative statements about the identifier (e.g. claim it by logging in).
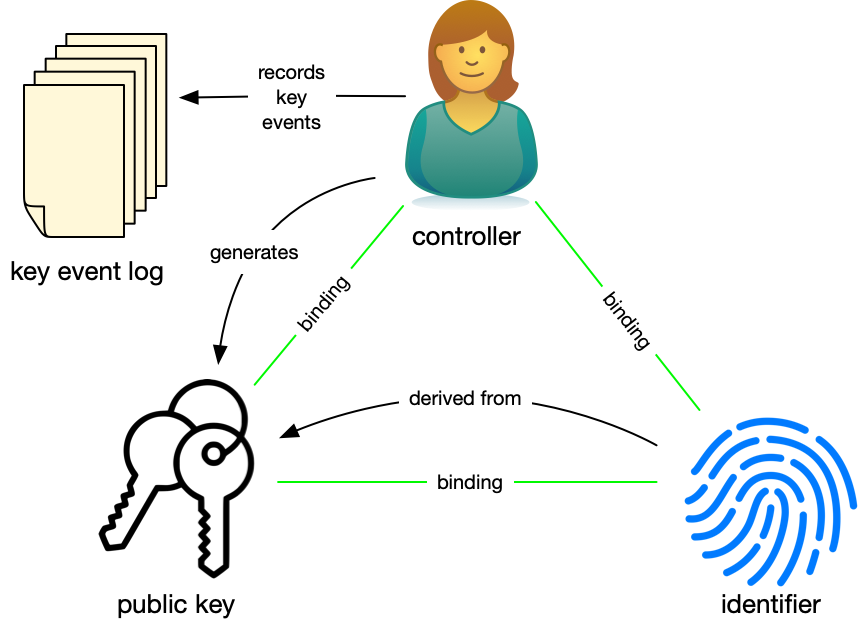
In an autonomic identity architecture, the controller, Alice, generates a public-private key pair, derives a globally unique identifier, and shares the identifier and the currently associated public key with others to create relationships. Alice uses her private key to sign statements that authenticate herself and authorize use of the identifier. A digital signature also provides the means for Alice to cryptographically respond to challenges so she can prove she controls the identifier. These self-authentication and self-authorization capabilities make the identifier self-certifying and self-managing, meaning that there is no external third party, not even a ledger, needed for Alice to manage and use the identifier and prove to others the integrity of the bindings between herself and the identifier.
Any entity can create and establish control over an identifier in a manner that is independent, interoperable, and portable without recourse to any central authority. Autonomic identity systems rely solely on self-sovereign authority.
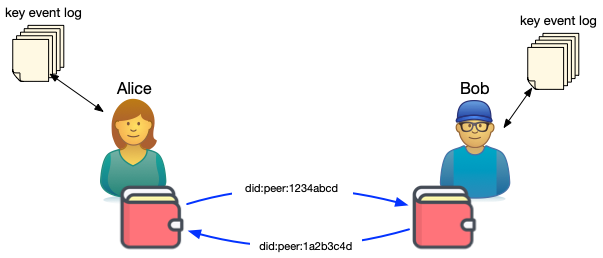
Alice can create as many Peer DIDs as she needs, each pointing to a public key that Alice controls. Alice can rotate the keys underneath the Peer DID anytime without impacting the identifier or her ability to prove she controls it. She keeps track of these key events in a key event log. The key event log is a chain of signed change records that can be cryptographically verified. Alice can use it to prove the provenance of her control of the identifier from its inception to the present.
Peer DID Exchange
Alice can exchange Peer DIDs with Bob to create a relationship. Because DIDs are associated with public keys, the exchange ensures that Alice and Bob have each other's public keys. They share key event logs (using a CRDT) for each identifier. If either updates the keys associated with the DID, the other is informed of change.
Having exchanged DIDs, Alice and Bob can now exchange signed and encrypted messages with each other using DIDComm. DIDComm is a messaging protocol that rides on top of this Peer DID relationship.
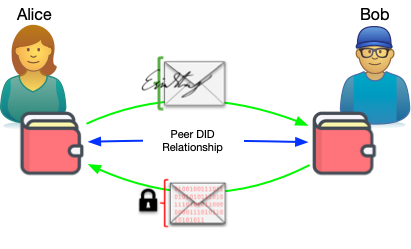
Alice and Bob are using digital wallets to store the keys (and manage their key event logs). The DIDComm messages are being exchanged using software agents that understand the DIDComm messaging protocol and use the keys in the wallet.
Alice can have DID-based relationships with multiple people, organizations, and even things. Each relationship includes a secure DIDComm-based messaging capability.
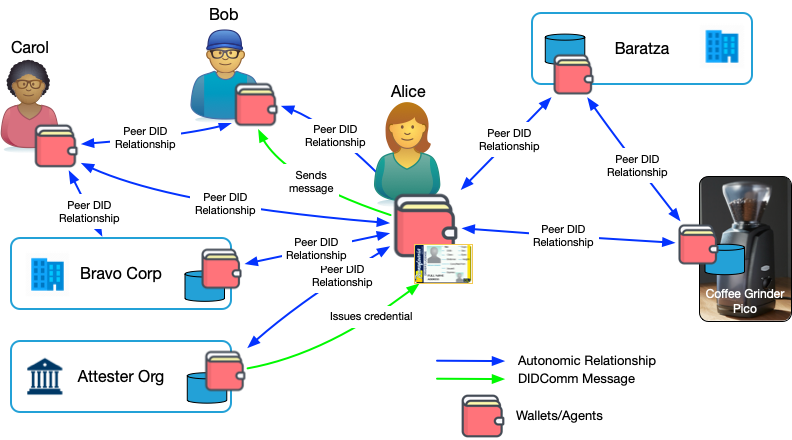
This network of DID-based relationships forms an overlay network. An overlay network comprises virtual links that correspond to a path in the underlying network. Secure overlay networks rely on an identity layer based on asymmetric key cryptography to ensure message integrity, non-repudiation, and confidentiality.
DIDComm messaging has several important properties that, taken together, provide a generative, secure network overlay for the Internet.
- Secure - DID-based relationships are mutually authenticating.
- Private - messages can be encrypted.
- Interoperable - messages can be exchanged between any agents that support the DIDComm protocol.
- Transport-agnostic - DIDComm does not rely on any specific network technology–it is as happy on Bluetooth as on TCP/IP or anything else.
- Extensible - DIDComm is designed to support other protocols riding on top of its general secure messaging infrastructure.
Protocological Power
The extensibility of DIDComm is one of its most powerful features because it makes DIDComm generative–just like the Internet itself.
Protocols describe the rules for a set of interactions, specifying the kinds of interactions that can happen without being overly prescriptive about their nature or content. Protocols formalize workflows for specific interactions like ordering food at a restaurant, playing a game, or applying for college.
The Hyperledger Aries project has a collection of RFCs that describe protocols for DIDComm messaging. While we have come to think of SSI agents being strictly about exchanging peer DIDs to create a connection, request and issue a credential, or prove things using credentials, these are merely specific protocols defined to run over the DIDComm messaging protocol. The follow specifications describe the protocols for these three core applications of DIDComm:
Dozens, even hundreds, of other protocols are possible.
Daniel Hardman has provided a comprehensive tutorial on defining protocols on DIDComm. One of the Aries RFCs is sample protocol definition of a protocol for playing TicTacToe over DIDComm messaging.
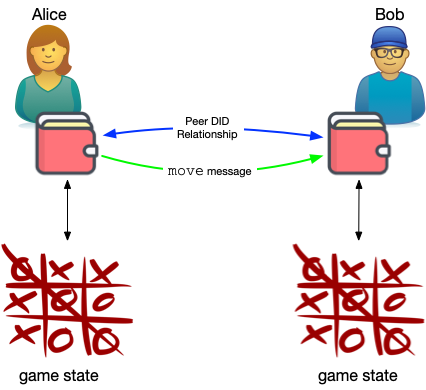
The TicTacToe protocol defines types of messages that are allowed, the game state, and what messages are allowed in each game state. I recommend it as a way to understand DIDComm protocols since it's familiar and easy to understand. Bruce Conrad who works on picos with me implemented the TicTacToe protocol for picos, which act as DIDComm agents.
Generativity
In 2005, Jonathan Zittrain wrote a compelling and prescient examination of the generative capacity of the Internet and its tens of millions of attached PCs. Zittrain defined generativity thus:
Generativity denotes a technology's overall capacity to produce unprompted change driven by large, varied, and uncoordinated audiences.From The Generative Internet
Referenced 2021-06-14T13:41:18-0600
Generative systems use a few basic rules, structures, or features to yield behaviors that can be extremely varied and unpredictable. Zittrain goes on to lay out the criteria for evaluating the generativity of a technology:
Generativity is a function of a technology's capacity for leverage across a range of tasks, adaptability to a range of different tasks, ease of mastery, and accessibility.
I have made the case elsewhere that the self-sovereign internet meets Zittrain's criteria for generativity.
Generativity provides decentralized actors with the ability to create cooperating, complex structures and behavior. No one person or group can or will think of all the possible uses, but each is free to adapt the system to their own use. The architecture of the self-sovereign internet enables adaptation of DIDComm messaging to any circumstance.
I am bullish on the possibilities for verifiable credentials to allow people to live digital lives with dignity and effectiveness, addresses the problems of social inclusion, and support economic equality to everyone around the globe. With all that, I believe the possibilities for the self-sovereign internet are even larger, promising a more secure and private, albeit no less useful, internet for tomorrow. DIDComm may turn out to be the most important part of self-sovereign identity.




