Summary
Self-sovereign identity, supported by a heterarchical identity metasystem, creates a firm foundation for rich digital relationships that allow people to be digitally embodied so they can act online as autonomous agents.

An earlier blog post, Relationships and Identity proposed that we build digital identity systems to create and manage relationships—not identities—and discussed the nature of digital relationships in terms of their integrity, lifespan, and utility. You should read that post before this one.
In his article Architecture Eats Culture Eats Strategy, Tim Bouma makes the point that the old management chestnut Culture Eats Strategy leaves open the question: how do we change the culture? Tim's point is that architecture (in the general sense) is the upstream predator to culture. Architecture is a powerful force that drives culture and therefore determines what strategies will succeed—or, more generally, what use cases are possible.
Following on Tim's insight, my thesis is that identity systems are the foundational layer of our digital ecosystem and therefore the architecture of digital identity systems drives online culture and ultimately what we can do and what we can't. Specifically, since identity systems are built to create and manage relationships, their architecture deeply impacts the kinds of relationships they support. And the quality of those relationships determines whether or not we live effective lives in the digital sphere.
Administrative Identity Systems Create Anemic Relationships
I was the founder and CTO of iMall, an early, pioneering ecommerce tools vendor. As early as 1996 we determined that we not only needed a shopping cart that kept track of a shopper's purchases in a single session, but one that knew who the shopper was from visit to visit so we could keep the shopping cart and pre-fill forms with shipping and billing addresses. Consequently, we built an identity system. In the spirit of the early web, it was a one-off, written in Perl and storing personal data in Berkeley DB. We did hash the passwords—we weren't idiots1.
Early Web companies had a problem: we needed to know things about people and there was no reliable way for them to tell us who they were. So everyone built an identity system and thus began my and your journey to collecting thousands of identifiers as the Web expanded and every single site needed it's own way to know things about us.
Administrative identity systems, as these kinds of identity systems are called, create a relationship between the organization operating the identity system and the people who are their customers, citizens, partners, and so on. They are, federation notwithstanding, largely self contained and put the administrator at the center as shown in Figure 1. This is their fundamental architecture.
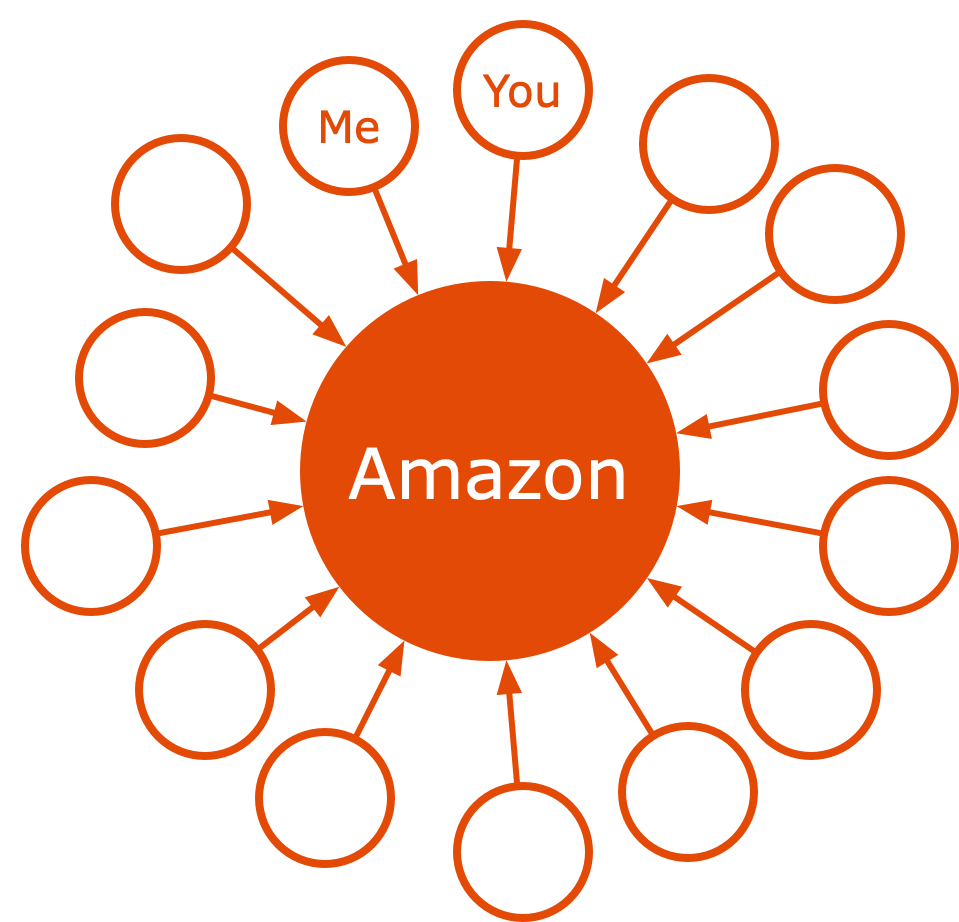
Administrative identity systems are owned. They are closed. They are run for the purposes of their owners, not the purposes of the people or things being administered. They provision and permission. They are bureaucracies for governing something. They rely on rules, procedures, and formal interaction patterns. Need a new password? Be sure to follow the password rules of what ever administrative system you're in. Fail to follow the company's terms of service? You could lose your account without recourse.
Administrative identity systems use a simple schema, containing just the attributes that the administrator needs to serve their purposes and reduce risk. The problem I and others were solving back in the 90's was legibility2. Legibility is a term used to describe how administrative systems make things governable by simplifying, inventorying, and rationalizing things around them. Identity systems make people legible in order to offer them continuity and convenience while reducing risk for the administrator.
Administrative identity systems give rise to a systematic inequality in the relationships they manage. Administrative identity systems create bureaucratic cultures. Every interaction you have online happens under the watchful eye of a bureaucracy built to govern the system and the people using it. The bureaucracy may be benevolent, benign, or malevolent but it controls the interaction.
Designers of administrative identity systems do the imaginative work of assigning identifiers, defining the administrative schemas and processes, and setting the purpose of the identity system and the relationships it engenders. Because of the systematic imbalance of power that administrative identity systems create, administrators can afford to be lazy. To the administrator, everyone is structurally the same, being fit into the same schema. This is efficient because they can afford to ignore all the qualities that make people unique and concentrate on just their business. Meanwhile subjects are left to perform the "interpretive labor" as David Graeber calls it of understanding the system, what it allows or doesn't, and how it can be bent to accomplish their goals. Subjects have few tools for managing these relationship because each one is a little different, not only technically, but procedurally as well. There is no common protocol or user experience. Consequently, subjects have no way to operationalize the relationship except in whatever manner the administrator allows.
Given that the architecture of administrative identity systems gives rise to a bureaucratic culture, what kinds of strategies or capabilities does that culture engender? Quoting David Graeber from The Utopia of Rules (pg 152):
Cold, impersonal, bureaucratic relations are much like cash transactions, and both offer similar advantages and disadvantages. On the one hand they are soulless. On the other, they are simple, predictable, and—within certain parameters, at least—treat everyone more or less the same.
I argue that this is the kind of thing the internet is best at. Our online relationships with ecommerce companies, social media providers, banks, and others are cold and impersonal, but also relatively efficient. In that sense, the web has kept its promise. But the institutionalized frame of action that has come to define it alienates its subjects in two ways:
- They are isolated and estranged from each other.
- They surrender control over their online activity and the associated data within a given domain to the administrator of that domain.
The administrative architecture and the bureaucratic culture it creates has several unavoidable, regrettable outcomes:
- Anemic relationships that limit the capabilities of the systems they support. For example, social media platforms are designed to allow people to form a link (symmetrical or asymmetrical) to others online. But it is all done within the sphere of the administrative domain of the system provider. The relationships in these systems are like two-dimensional cardboard cutouts of the real relationships they mirror. We inhabit multiple walled gardens that no more reflect real life than do the walled gardens of amusement parks.
- A surveillance economy that relies on the weak privacy provisions that administrative systems create to exploit our online behavior as the raw material for products that not only predict, but attempt to manipulate, our future behaviors.3 Many administrative relationships are set up to harvest data about our online behavior. The administrator controls the nature of these relationships: what is allowed and what behavior is rewarded.
- Single points of failure where key parts of our lives are contained within the systems of companies that will inevitably cease to exist someday. In the words of Craig Burton: "It's about choice: freedom of choice vs. prescribed options. Leadership shifts. Policies expire. Companies fail. Systems decay. Give me the freedom of choice to minimize these hazards."
The Self-Sovereign Alternative
Self-sovereign identity (SSI) systems offers an alternative model that supports richer relationships. Rather than provisioning identifiers and accounts in an administrative system where the power imbalance assures that one party to the relationship can dictate the terms of the interaction, SSI is founded on peer relationships that are co-provisioned by the exchange of decentralized identifiers. This architecture implies that both parties will have tools that speak a common protocol.
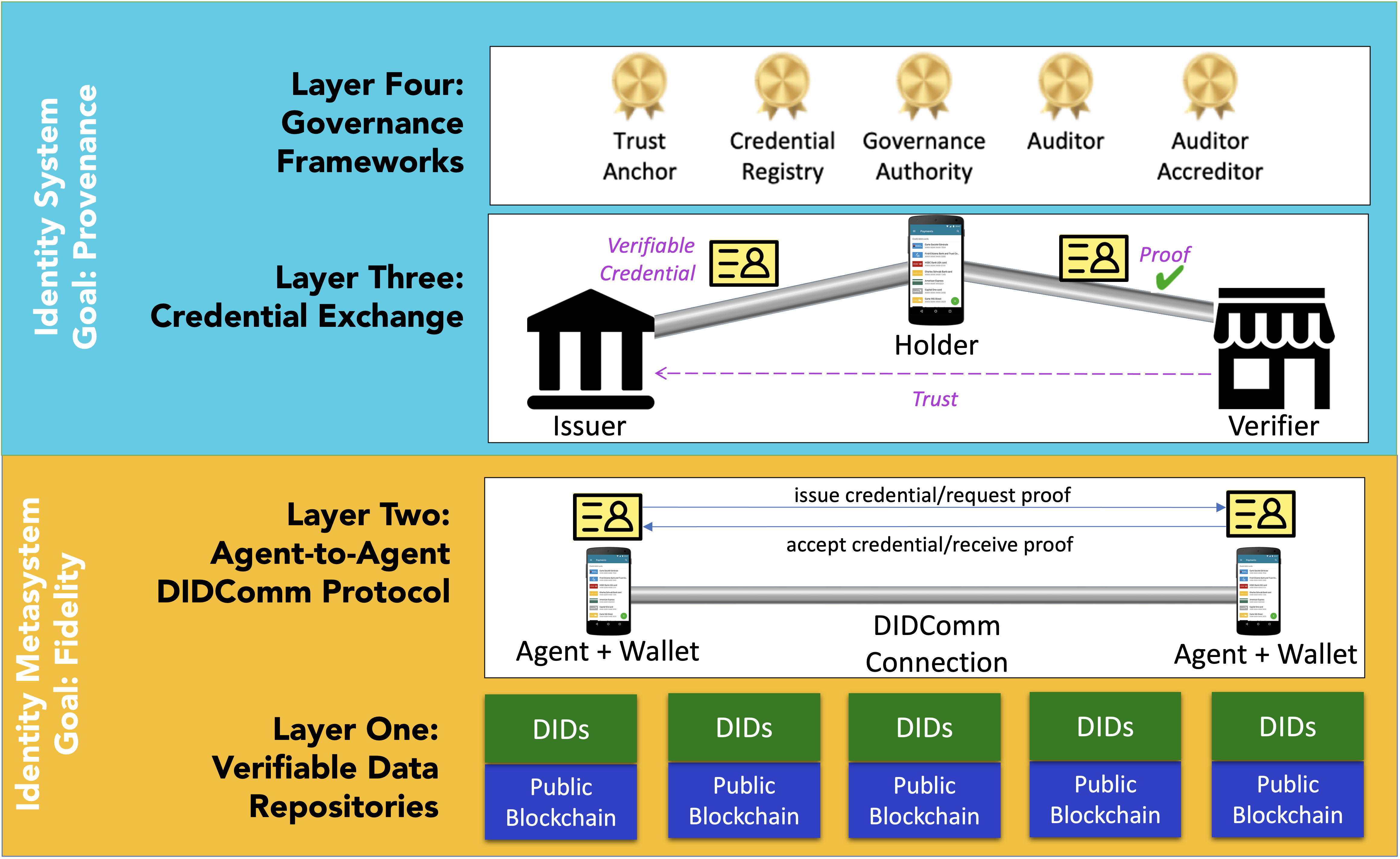
Figure 2 shows the self-sovereign identity stack. The bottom two layers, the Verifiable Data Repositories and the Peer-to-Peer Agents make up what we refer to as the Identity Metasystem. The features of the metasystem architecture are our primary interest. I have written extensively about the details of the architecture of the metasystem in other posts (see The Sovrin SSI Stack and Decentralized Identifiers).
The architecture of the metasystem has several important features:
- Mediated by protocol—Instead of being intermediated by an intervening administrative authority, activities in the metasystem are mediated through peer-to-peer protocol. Protocols are the foundation of interoperability and allow for scale. Protocols describe the rules for a set of interactions, specifying the kinds of interactions that can happen without being overly prescriptive about their nature or content. Consequently, the metasystem supports a flexible set of interactions that can be adapted for many different contexts and needs.
- Heterarchical—Interactions in the metasystem are peer-to-peer rather than hierarchical. The are not just distributed, but decentralized. Decentralization enables autonomy and flexibility and to assure its independence from the influence of any single actor. No centralized system can anticipate all the various use cases. And no single actor should be allowed to determine who uses the system or for what purposes.
- Consistent user experience—A consistent user experience doesn’t mean a single user interface. Rather the focus is on the experience. As an example, consider an automobile. My grandfather, who died in 1955, could get in a modern car and, with only a little instruction, successfully drive it. Consistent user experiences let people know what to expect so they can intuitively understand how to interact in any given situation regardless of context.
- Polymorphic—The information we need in any given relationship varies widely with context. The content that an identity metasystem carries must be flexible enough to support many different situations.
These architectural features give rise to a culture that I describe as protocological. The protocological culture of the identity metasystem has the following properties:
- Open and permissionless—The metasystem has the same three virtues of the Internet that Doc Searls and Dave Weinberger enumerated as NEA: No one owns it, Everyone can use it, and Anyone can improve it. Special care is taken to ensure that the metasystem is censorship resistant so that everyone has access. The protocols and code that enable the metasystem are open source and available for review and improvement.
- Agentic—The metasystem allows allows people to act as autonomous agents, under their self-sovereign authority. The most vital value proposition of self-sovereign identity is autonomy—not being inside someone else's administrative system where they make the rules in a one sided way. Autonomy requires that participants interact as peers in the system, which the architecture of the metasystem supports.
- Inclusive—Inclusivity is more than being open and permissionless. Inclusivity requires design that ensures people are not left behind. For example, some people cannot act for themselves for legal (e.g. minors) or other (e.g. refugees) reasons. Support for digital guardianship ensures that those who cannot act for themselves can still participate.
- Flexible—The metasystem allows people to select appropriate service providers and features. No single system can anticipate all the scenarios that will be required for billions of individuals to live their own effective lives. A metasystem allows for context-specific scenarios.
- Modular—An identity metasystem can’t be a single, centralized system from a single vendor with limited pieces and parts. Rather, the metasystem will have interchangeable parts, built and operated by various parties. Protocols and standards enable this. Modularity supports substitutability, a key factor in autonomy and flexibility.
- Universal—Successful protocols eat other protocols until only one survives. An identity metasystem based on protocol will have network effects that drive interoperability leading to universality. This doesn't mean that one organization will have control, it means that one protocol will mediate all interaction and everyone in the ecosystem will conform to it.
Supporting Authentic Relationships
Self-sovereign identity envisions digital life that cannot be supported with traditional identity architectures. The architecture of self-sovereign identity and the culture that springs from it support richer, more authentic relationships:
- Self-sovereign identity provides people with the means of operationalizing their online relationships by providing them the tools for acting online as peers and managing the relationships they enter into.
- Self-sovereign identity, through protocol, allows ad hoc interactions that were not or cannot be imagined a priori.
The following subsections give examples for each of these.
Disintermediating Platforms
Many real-world experiences have been successfully digitized, but the resulting intermediation opens us to exploitation despite the conveniences. We need digitized experiences that respect human dignity and don't leave us open to being exploited for some company's advantage. As an example consider how the identity metasystem could be the foundation for a system that disintermediates the food delivery platforms. Platform companies have been very successful in intermediating these exchanges and charging exorbitant rents for what ought to be a natural interaction among peers.
That's not to say platforms provide no value. The problem isn't that they charge for services, but that their intervening position gives them too much power to make markets and set prices. Platforms provide several things that make them valuable to participants: a means of discovering relevant service providers, a system to facilitate the transaction, and a trust framework to help participants make the leap over the trust gap, as Rachel Botsman puts it. An identity metasystem supporting self-sovereign identity provides a universal trust framework for building systems that can serve as the foundation for creating markets without intermediaries. Such a system with support for a token can even facilitate the transaction without anyone having an intervening position.
Disintermediating platforms requires creating a peer-to-peer marketplace on top of the metasystem. While the metasystem provides the means of creating and managing the peer-to-peer relationship, defining this marketplace requires determining the messages to be exchanged between participants and creating the means of discovery. These messages might be simple or complex depending on the market and could be exchanged using DIDComm, or even ride on top of a verifiable credential exchange. There might be businesses that provide discovery, but they don't intermediate, they sit to the side of the interaction providing a service. For example, such a business might provide a service that allows a restaurant to define its menu, create a shopping cart, and provide for discovery, but the merchant could replace it with a similar service, providing competition, because the trust interaction and transaction are happening via a protocol built on a universal metasystem.
Building markets without intermediaries greatly reduces the cost of participating in the market and frees participants to innovate. Because these results are achieved through protocol, we do not need to create new regulations that stifle innovation and lock in incumbents by making it difficult for new entrants to comply. And these systems preserve human dignity and autonomy by removing administrative authorities.
Digitizing Auto Accidents
As an example of the the kinds of interactions that people have every day that are difficult to bring into the administrative sphere, consider the interactions that occur between various participants and their representatives following an auto accident. Because these interactions are ad hoc, large parts of our lives have yet to enjoy the convenience of being digitized. In You've Had an Automobile Accident, I imagine a digital identity system that enables the kinds of ad hoc, messy, and unpredictable interactions that happen all the time in the physical world.
In this scenario, two drivers, Alice and Bob, have had an accident. Fortunately, no one was hurt, but the highway patrol has come to the scene to make an accident report. Both Alice and Bob have a number of credentials that will be necessary to create the report:
- Proof of insurance issued by their respective insurance companies
- Vehicle title from the state
- Vehicle registration issued by the Department of Motor Vehicles (DMV) in different states (potentially)
- Driver's license, potentially from a different agencies than the one who registers cars and potentially in different states
In addition, the police officer has credentials from the Highway Patrol, Alice and Bob will make and sign statements, and the police officer will create an accident report. What's more, the owners of the vehicles may not be the drivers.
Now imagine you're building a startup to solve the "car accident use case." You imagine a platform to relate to all these participants and intermediate the exchange of all this information. To have value, it has to do more than provide a way to exchange PDFs and most if not all of the participants have to be on it. The system has to make the information usable. How do you get all the various insurance companies, state agencies, to say nothing of the many body shops and hospitals, fire departments, and ambulance companies on board? And yet, these kinds of ad hoc interactions confront us daily.
Taking our Rightful Place in the Digital Sphere
Devon Leffreto said something recently that made me think:
You do not have an accurate operational relationship with your Government.
My thought was "not just government". The key word is "operational". People don't have operational relationships anywhere online.4 We have plenty of online relationships, but they are not operational because we are prevented from acting by their anemic natures. Our helplessness is the result of the power imbalance that is inherent in bureaucratic relationships. The solution to the anemic relationships created by administrative identity systems is to provide people with the tools they need to operationalize their self-sovereign authority and act as peers with others online. Scenarios like the ones envisioned in the preceding section happen all the time in the physical world—in fact they're the norm. When we dine at a restaurant or shop at a store in the physical world, we do not do so under some administrative system. Rather, as embodied agents, we operationalize our relationships, whether they be long-lived or nascent, by acting for ourselves. An identity metasystem provides people with the tools they need to be "embodied" in the digital world and act autonomously.
Time and again, various people have tried to create decentralized marketplaces or social networks only to fail to gain traction. These systems fail because they are not based on a firm foundation that allows people to act in relationships with sovereign authority in systems mediated through protocol rather than companies. We have a fine example of a protocol mediated system in the internet, but we've failed to take up the daunting task of building the same kind of system for identity. Consequently, when we act, we do so without firm footing or sufficient leverage.
Ironically, the internet broke down the walled gardens of CompuServe and Prodigy with a protocol-mediated metasystem, but surveillance capitalism has rebuilt them on the web. No one could live an effective life in an amusement park. Similarly, we cannot function as fully embodied agents in the digital sphere within the administrative systems of surveillance capitalists, despite their attractions. The emergence of self-sovereign identity, agreements on protocols, and the creation of a metasystem to operationalize them promises a digital world where decentralized interactions create life-like online experiences. The identity metasystem and the richer relationships that result from it promise an online future that gives people the opportunity to act for themselves as autonomous human beings and supports their dignity so that they can live an effective online life.
End Notes
- Two of my friends at the time, Eric Thompson and Stacey Son were playing with FPGAs that could crack hashed passwords, so we were aware of the problems and did our best to mitigate them.
- See Venkatesh Rao's nice summary of James C. Scott's seminal book on legibility and its unintended consequences, Seeing Like a State for more on this idea.
- See The Age of Surveillance Capitalism by Shoshana Zuboff for a detailed (705 page) exploration of this idea.
- The one exception I can think of to this is email. People act through email all the time in ways that aren't intermediated by their email provider. Again, it's a result of the architecture of email, set up over four decades ago and the culture that architecture supports.
Photo Credit: Two Yellow Bees from Pikrepo (public)




